Criminals are targeting customers of outsourcer ADP with a dangerous Java exploit in a bid to steal employee personal and financial details.
The phishing attacks attempt to direct company payroll administrators to malicious websites rigged with exploit kits, including the recently patched Java Runtime Environment (JRE) HotSpot hole (CVE-2012-1723).
The kits were encrypted and detected by only eight of the 41 anti-virus vendors on VirusTotal.
One attack reported by some of ADP’s 600,000 customers attempted to con users with warnings that the company’s digital certificate was close to expiry.
ADP issued an advisory (pdf) warning customers of the attacks and pledging to track down the offenders.
Some of the company's 7000 Australian and New Zealand customers include Beacon Lighting, YMCA Victoria and Turi Foods.
SANS incident handler Daniel Wesemann recommended customers secure the Java hole and warn staff.
“Make sure your HR and payroll folks are treated to another round of ‘don’t click on this link’ training. They are your first line of defence, and - given anti-virus' ineffectiveness - usually even your only line of defence,” Wesemann said.
Customers should examine email logs to learn the distinction between legitimate mail and phishing scams, he said.
“This knowledge is priceless during an incident, and might even help you to automatically block some of the more egregious phishes.”
Wesemann said users should uninstall the JRE if possible.
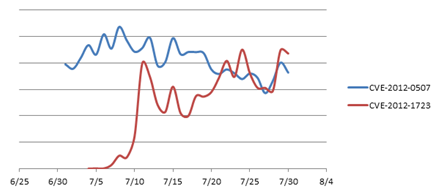
The scam is the latest of a boom in attacks exploiting CVE2012-1723 over the last month. Attacks had overtaken the previous major JRE hole (CVE-2012-0507) according to Microsoft malware analyst Jeong Wook.
The nature of the vulnerability meant that attackers could not hide the internals of exploit, making analysis easier. That made the hole less popular to malware writers, but hadn’t stymied interest.
Wook posted a technical analysis of the exploit and details on how to disable JRE.



.jpg&h=140&w=231&c=1&s=0)





















