Password and credentials manager LastPass is taking urgent measures to protect its users after the company discovered an unauthorised data disclosure on its network.
Chief executive Joe Siegrist revealed LastPass had discovered and blocked suspicious activity on its network over the weekend and begun an investigation into the matter.
The investigation revealed LastPass account email addresses, password reminders, server per-user salts (added random characters to make it more difficult for attackers to guess data values), as well as authentication hashes (shortened, fixed-length character strings that represent longer, original values) were compromised, Siegrist wrote.
He said there was no evidence so far that encrypted user vault data was taken or that LastPass user accounts were accessed.
While LastPass remained confident that its current encryption measures were strong enough to protect the vast majority of its users, Siegrist said the company will ask users who log in from new devices or different IP addresses to verify their accounts via email.
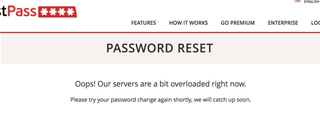
Siegrist said users will also be asked to update their master passwords. As of writing, it appears users are following that advice in large numbers, overloading LastPass servers'.
There is no need to update passwords for sites stored in LastPass vaults however, as no encrypted data was captured, Siegrist said
He recommended LastPass users enable multifactor authentication on their accounts for further protection.
Siegrist did not say who LastPass suspected was behind the data breach, but said the company is working with law enforcement and IT security forensic experts on the issue.
LastPass was founded in 2008 and offers free clients for Windows, Apple OS X, Linux, iOS and Android, and paid premium and enterprise apps with a fuller range of features.
In 2011, LastPass urgently warned its users to change passwords following a suspected security breach. The company later bolstered security measures by strengthening encryption and authentications hashing.



.png&h=140&w=231&c=1&s=0)






















