ANZ Banking Group is looking to expand its use of a Google cloud tool, presently used to check if computer code meets certain standards before being put into production, to perform similar automated checkboxing in its risk and regulatory compliance functions.
Back in April, the bank revealed it is using a tool called binary authorisation to prevent unauthorised code and container images from being deployed to production.
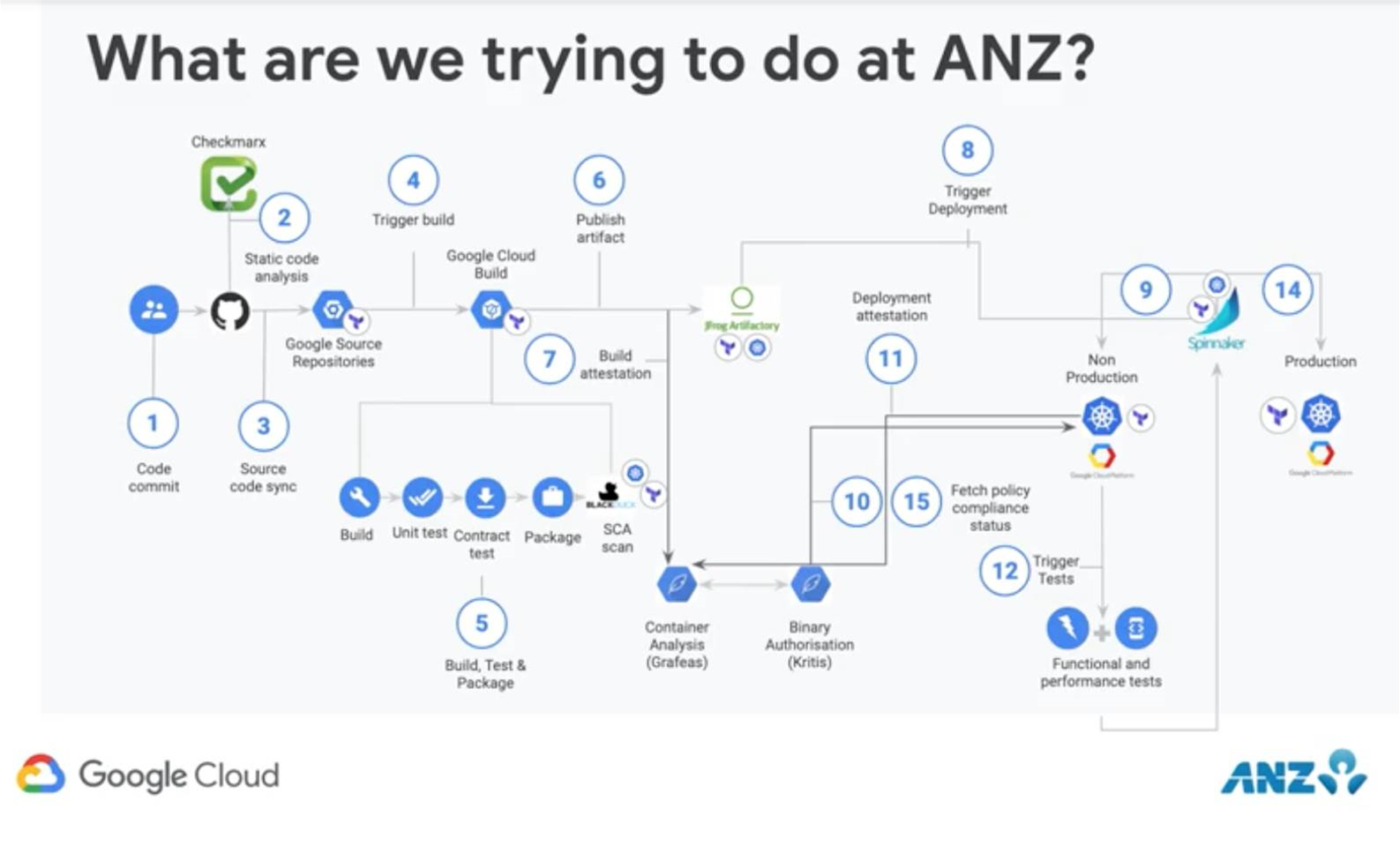
The tool automatically checks whether the code or container image has passed internal checks set for various stages of deployment; only those that pass are allowed through to production.
Always a cost burden for banks, regulatory related expenses at Australian institutions have soared over the last 12 months on the back of the Royal Commission and its exposure of rafts of defective or substandard compliance that are now being remedied.
The high cost of remediation of compliance platforms is amplified by the fact that there is often little direct RoI from development efforts aside from complying with the law, unlike other systems builds that drive profit.
ANZ senior product owner Rakesh Garala told a Google Cloud event last week that the bank wanted to move faster with containerisation and code deployment, albeit in a safe and secure manner.
“The opportunity for us is to look at whether or not we can create industrialised CI/CD [continuous integration/continuous deployment] capabilities or ‘paved roads’ as we call them, and look at whether or not they can essentially … give engineers a faster and [more] transparent way to get their code to customers and most importantly to get immediate and transparent feedback on where their code doesn’t actually make it through to production,” Garala said.
The bank initially saw binary authorisation as a way to make sure that code passing through its CI/CD pipeline met certain standards.
Garala said there was a “level of complexity” present in the bank’s CI/CD pipeline.
“On the left hand side you’re seeing an engineer commit code, on the right hand side you’re seeing a tool called Spinnaker deploy that into production, and you have various things inbetween: you have static code scanning, artefact management,” he said.
“There’s things that we’ve evolved further from this. We’re using vulnerability scanning like Twistlock, we’re using Black Duck for certain aspects of code scanning.
“[But] the tools don’t matter. What matters is these key capabilities that you require to ensure that something that moves through your pipeline meets a set of operational standards that you would expect from your technology.”
Binary authorisation in this instance defines a “paved road” that code has to travel before it can be approved to run in production.
“The numbers represent key attestations or key ticks that we expect to see [on that road],” Garala said.
Garala noted that there could be separate “paved roads” for production and non-production environments, and even different roads enforced by binary authorisation within those domains.
But the bank is also looking more broadly at where the binary authorisation tool might come in handy outside of code approval.
Specifically, Garala mentioned several parts of the bank where this kind of checkboxing is a requirement, and therefore where the introduction of cloud-based automation could be helpful.
“We have been thinking about can we start to use this for automated governance,” he said.
“But can we go one step further - as an organisation can we start to use this to do our governance and potentially some of our risk appetite? Is there a different way that we can think about our internal governance and some of our processes? Could we set guardrails that are enforced by binary authorisation?”
Further down the track, ANZ also considers regulatory compliance as another potential use case.
“Potentially down the line, is there a way for us to rethink and use some of this technology and some of these capabilities to think about how we do regulatory compliance and to demonstrate our adherence to regulators’ requirements around the globe?” Garala said.
“Could we use binary authorisation to set ourselves particular guardrails that keep us within regulatory compliance?”
Google hits its stride
Garala said that Google and ANZ are working closely on augmenting binary authorisation and other Google cloud platform (GCP) tools, though the cooperation was a relatively new feature of the relationship between the pair.
“I will be very frank and honest. We started a year and a half ago, and to be very frank GCP was far behind your competitors,” Garala said.
“That resulted in a couple of things for us. One was we were struggling with the technology because it wasn’t really fit at that point, and two we felt isolated.
“We didn’t have the level of interaction and the support we felt we wanted or required.”
Garala said that started to dissipate when ANZ realised where Google was at with the development of GCP - and its openness to collaborate.
“What we identified pretty quickly was actually what Google was learning about what customers wanted, and actually starting to build this product out and doing the right thing - using a product mindset to get something out there and starting to iterate that product out,” he said.
“What that has meant for us is that we have been able to work very closely with Google’s product and development teams.
“Binary authorisation is a really good example. We’ve been working directly with the team building that product to actually give our customer requirements to those products and starting to iterate that product out together.”
Garala noted the cooperation and co-creation on GCP products “continues today”.
“We’re actually working with a range of other parts of [Google] to help influence and maybe contribute to what the products need to look like,” he said.
The bank was recently partially responsible for bringing out renowned Kubernetes expert and Googler Kelsey Hightower to Australia.
It held a series of private workshops for staff aimed at improving its containerisation practices.





.png&h=140&w=231&c=1&s=0)




















