The Australian National University says it has been able to help other unnamed universities "fend off attacks" using new capabilities it set up in the early part of a five-year information security program.
The program, described at a high level in a parliamentary submission released at the end of last year, comes after ANU was targeted by an advanced persistent threat (APT) actor that led to two data breaches.
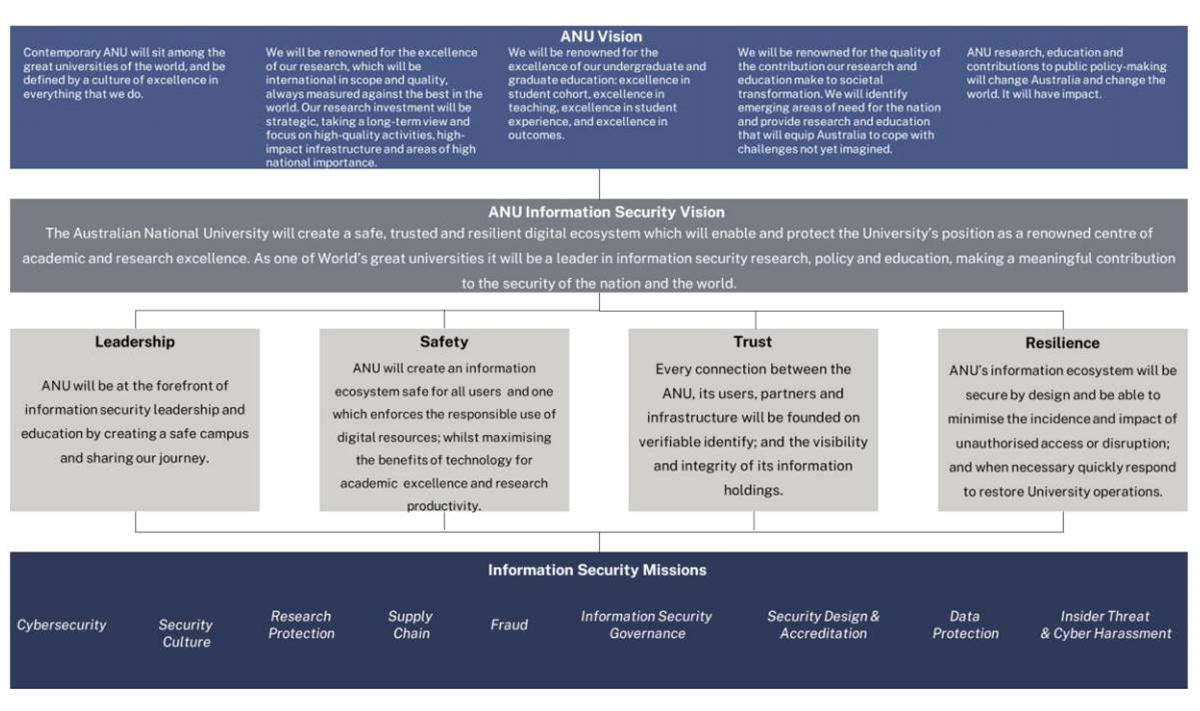
ANU said [pdf] it had started the information security program “in early 2020” and is targeting wide-ranging improvements in domains such as cyber security, supply chain security, insider threat, governance, design and culture.
Although only a year into a five-year program of work, the university said it had a “growing security workforce and a purpose-built facility - the Information Security Office - dedicated to foreign interference and cyber security.”
ANU also claimed some early wins.
“During the first year of the program, ANU deployed a range of operational capabilities that have not only helped secure our community but also fended off attacks on other universities and assisted government agencies,” ANU said.
“To the best of our knowledge, there is no comparable capability - one that covers the above mission areas under a single command structure with direct reporting oversight by a vice-chancellor - across the Five-Eyes.”
The Five-Eyes is a reference to the signals intelligence alliance of authorities in Australia, Canada, New Zealand, the UK and US.
ANU said that part of the five-year program of works was aimed at reducing the threats posed by foreign interference in the higher education and research sector, which is the topic of a federal inquiry.
In a submission to that inquiry, the ANU said it had appointed its CISO Suthagar Seevaratnum as its “chief security officer (CSO) for foreign interference.”
There were several “common vectors” for foreign interference seen either on-campus or in the sector, including “cyber operations, research interference or human and policy-based operations,” the university said.
On that front, ANU said it has set a “target state to implement the so-called ASD Top 37 mitigations (which includes the essential eight) by the end of 2022”.
The mitigations are used in and outside government as a benchmark for cyber resiliency, with most organisations setting targets of ‘top four’ or ‘essential eight’ proficiency.
Aside from the target state, ANU provided little other detail on the five-year program other than a general overview of its aims and intentions, as well as the various security domains it intends to revamp.
It did, however, state that it continues to be “an ongoing target for foreign actors”, in part due to its “proximity to government”.
“While we openly acknowledge [that we] are a high-value target within the sector for foreign interference, we are not alone,” ANU said.
“Our experience shows that actors will engage in ‘institution shopping’ between universities and undertake a range of tradecraft to achieve their goals.
“To combat this, there must be an open, fast and free flow of information between universities and with security agencies so that there is a natural and agile response to such attempts.”





.png&h=140&w=231&c=1&s=0)




















