The Cost of a Data Breach report for 2021 was recently released by IBM and The Ponemon Institute. Yes, the costs went up again, with the average total cost of a data breach increasing by nearly 10 percent year over year, the largest single year cost increase in the last seven years.
Data breach costs rose from US$3.86 million to US$4.24 million, the highest average total cost in the history of this report. And across the Asia Pacific region, we saw an average 12 percent increase in the cost of data breaches across all participating regions.
Globally, compromised credentials was the hardest nut to crack, with survey respondents taking over 250 days to find an attack of this nature and 91 days to contain such an attack (followed by BEC compromise and malicious insider). This makes it imperative that we continue to focus on multi-factor authentication as a critical service deployed within client environments.
In Australia, the average cost of a data breach hit an all-time high for the last 12 years. What was also concerning was that the average time to detect and contain a data breach was 311 days t- which is more than a week longer than the time reported the previous year. This indicates that not only are security threats getting more complicated but the rapid shift to remote operations during the pandemic has led to more expensive data breaches. In fact, Australian companies with more than 50 percent remote work adoption took 325 days to identify and contain a data breach.
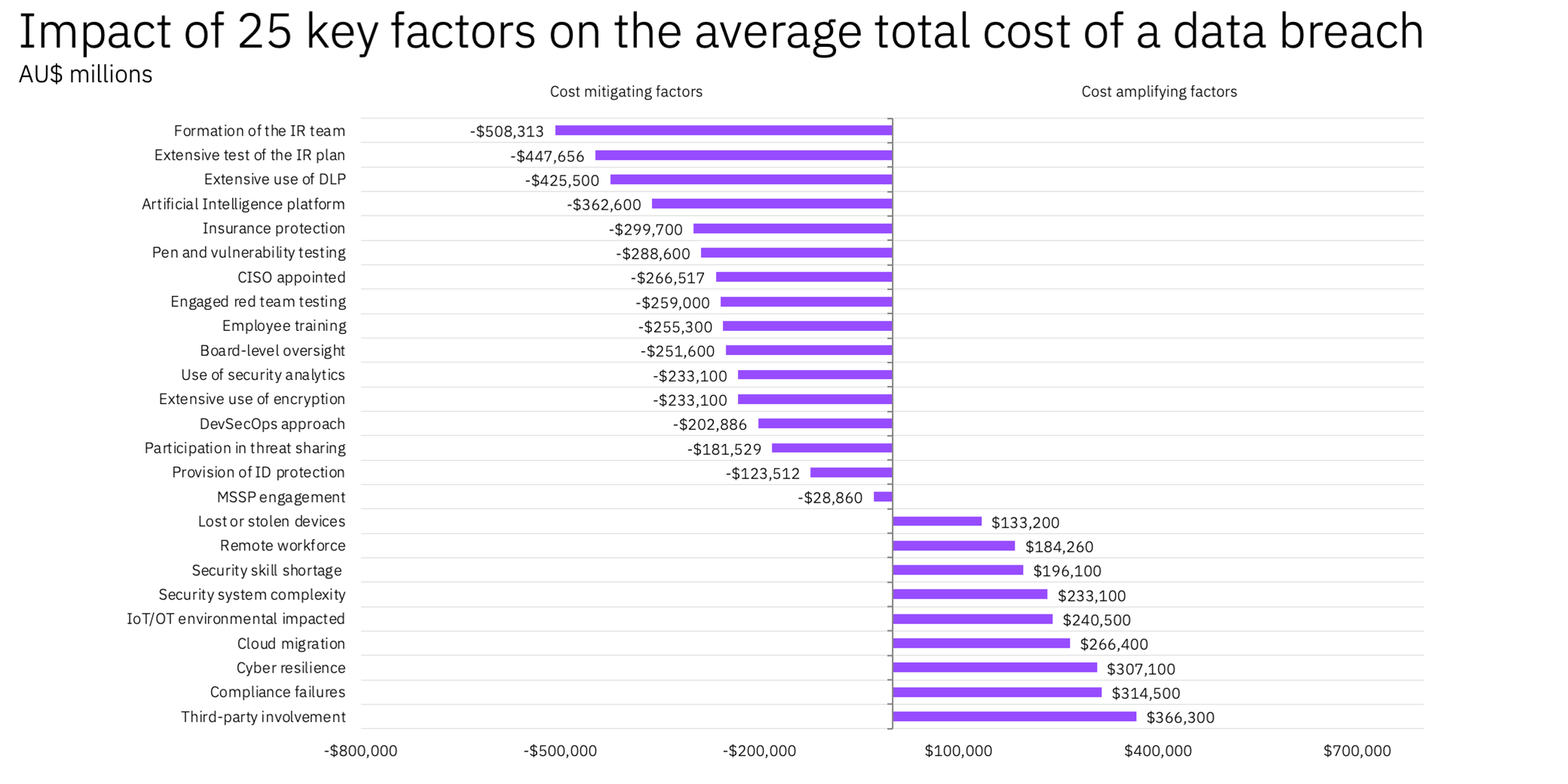
The following chart provides an exclusive view of the top factors that contributed to the total cost of data breaches in Australia.
From an industry standpoint, data breaches globally in the financial sector were most expensive (costing AU$233 per record), followed by breaches in the technology sector and services.
Areas where we see some improvements were organisations in various stages of adoption of a zero trust security approach. These Australian companies were found to be better positioned to deal with data breaches – those with a mature zero trust strategy had an average data breach cost of AU$2.73 million – AU$1.54 million lower than those who had not deployed this approach at all. In addition, organisations that had implemented a hybrid cloud approach were able to identify and contain a data breach faster in 266 days, a staggering 80 days sooner than those with a primarily public cloud approach (346 days). If you would like to meet our experts for a deep-dive into the cost of data breach for the Australian market, please reach out to us here.
Globally, the average cost of data breaches in mature zero trust deployments was US$1.73M lower than for organisations which haven’t yet started yet. The detailed global Cost of Data Breach Report can be accessed here.
There are a few recommendations based on the findings of the report that I find immensely appropriate for Australian organisations:
- Adopt a zero trust security model to help prevent unauthorised access to sensitive data: Controls such as multi-factor authentication can form the basis of a number of integrated zero trust scenarios.
- Invest in security orchestration, automation and response (SOAR) to help improve detection and response times: Security AI and automation significantly reduced the average time to identify and respond to a data breach and had a lower average cost.
- Stress test your incident response plan to increase cyber resilience and use tools that help protect and monitor endpoints and remote employees: Unified endpoint management (UEM) and identity and access management (IAM) products and services can help provide security teams with deeper visibility into suspicious activity.
- Invest in governance, risk management and compliance programs: Methodologies such as FAIR risk quantification can help to quantify the cost of a potential breach and help in the decision-making process for allocating resources.
- Embrace an open security architecture and minimise the complexity of IT and security environments: Security tools with the ability to share data between disparate systems (coupled with a managed security services provider) can help security teams detect incidents across complex hybrid multi-cloud environments.
- Protect sensitive data in cloud environments using policy and encryption: With the increasing amount and value of data being hosted in cloud environments, organisations should take steps to protect cloud-hosted databases.
Access the detailed global Cost of Data Breach Report here.
About the Author

Chris Hockings
Master Inventor and ANZ CTO
IBM Security
Chris Hockings is recognised as an IBM Master Inventor and Regional CTO for IBM Security A/NZ, with sustained contribution to IBM Security’s US patent portfolio. He is responsible for representing the IBM global security innovation strategy and vision to the A/NZ market, engaging with leaders across the industry and driving innovative partnerships with clients on emerging technology. Chris brings his extensive client experience and thought leadership to the IBM Security Australia Research and Development facility, to help the lab design and develop globally competitive offerings across cyber security products and services.